Navigating Data Protection in 2025: Essential Strategies for Businesses to Safeguard Sensitive Information
Introduction
As we move further into 2025, the landscape of data protection continues to evolve at an unprecedented pace. With increasing regulatory demands, growing cybersecurity threats, and heightened consumer awareness about privacy, businesses must prioritize the safeguarding of sensitive information. This article outlines essential strategies for navigating data protection in 2025, helping organizations effectively manage risks and build trust with their customers.
The Importance of Data Protection
Data protection is no longer just a compliance requirement; it has become a critical component of business strategy. Organizations that fail to protect sensitive information not only risk facing hefty fines but also jeopardize their reputation and customer trust. In a world where data breaches are increasingly common, businesses must take proactive steps to secure their data assets.
Understanding Regulatory Frameworks
In 2025, various global regulations govern data protection, including the General Data Protection Regulation (GDPR) in Europe, the California Consumer Privacy Act (CCPA) in the United States, and many others worldwide. It is essential for businesses to stay informed about these regulations and ensure compliance to avoid legal repercussions. Understanding the nuances of each regulation can provide businesses with a competitive edge while minimizing risks.
Adopting a Data Protection Framework
To navigate the complexities of data protection, organizations should adopt a comprehensive data protection framework. This framework should encompass policies, procedures, and technologies designed to safeguard sensitive information. Key components of an effective data protection framework include:
1. Data Classification
Businesses must implement a data classification system to identify and categorize sensitive information. This allows organizations to apply appropriate security measures based on the level of risk associated with different data types.
2. Risk Assessment
Regular risk assessments are crucial for identifying potential vulnerabilities in an organization's data protection strategy. By assessing risks, businesses can prioritize their efforts and allocate resources effectively to mitigate potential threats.
3. Incident Response Plan
An incident response plan outlines the steps an organization will take in the event of a data breach or security incident. This plan should include communication strategies, roles and responsibilities, and recovery procedures to minimize the impact of a breach.
Implementing Robust Security Measures
In 2025, cyber threats are more sophisticated than ever, making robust security measures essential for protecting sensitive information. Businesses should consider the following strategies:
1. Encryption
Encryption is a critical technology for safeguarding data both at rest and in transit. By converting sensitive information into unreadable code, organizations can protect data from unauthorized access, ensuring that even if a breach occurs, the data remains secure.
2. Multi-Factor Authentication (MFA)
MFA adds an additional layer of security by requiring users to provide two or more verification factors before accessing sensitive information. This significantly reduces the risk of unauthorized access and enhances overall data security.
3. Regular Software Updates
Keeping software and systems up to date is crucial for protecting against vulnerabilities. Businesses should implement a regular patch management process to ensure that all software is updated promptly, reducing the risk of exploitation by cybercriminals.
Employee Training and Awareness
Employees play a vital role in any data protection strategy. In 2025, organizations must prioritize ongoing training and awareness programs to equip their workforce with the knowledge needed to recognize and respond to data security threats. Key areas to focus on include:
1. Phishing Awareness
Phishing attacks remain one of the most common methods used by cybercriminals to gain unauthorized access to sensitive information. Employees should be trained to recognize phishing emails and suspicious links, and they should know how to report such incidents.
2. Data Handling Best Practices
Employees should be educated on the best practices for handling sensitive information, including data minimization, secure storage, and proper disposal methods. This knowledge empowers employees to take responsibility for protecting company data.
Leveraging Technology for Data Protection
Technology plays a crucial role in enhancing data protection efforts. Businesses in 2025 can leverage various tools and solutions to safeguard sensitive information:
1. Data Loss Prevention (DLP) Solutions
DLP solutions help organizations monitor and protect sensitive data from unauthorized access and leaks. By implementing DLP tools, businesses can enforce policies that prevent the sharing of sensitive information outside the organization.
2. Security Information and Event Management (SIEM) Systems
SIEM systems provide real-time analysis of security alerts generated by applications and network hardware. By utilizing SIEM tools, organizations can detect and respond to potential threats more effectively, enhancing their overall security posture.
3. Cloud Security Solutions
As more businesses migrate to cloud-based services, securing cloud environments becomes paramount. Organizations should consider implementing cloud security solutions that offer features such as encryption, access controls, and monitoring to protect sensitive data stored in the cloud.
Building a Culture of Data Protection
Creating a culture of data protection within an organization is essential for ensuring long-term success in safeguarding sensitive information. Businesses should foster an environment where data protection is prioritized at all levels:
1. Leadership Commitment
Leadership must demonstrate a commitment to data protection by establishing clear policies and supporting initiatives that prioritize security. When leaders prioritize data protection, it sets the tone for the entire organization.
2. Cross-Department Collaboration
Data protection is not solely the responsibility of the IT department; it requires collaboration across all departments. Businesses should encourage communication and teamwork between IT, legal, HR, and other departments to create a holistic approach to data protection.
Staying Ahead of Emerging Threats
The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Businesses must remain vigilant and adaptable to stay ahead of potential risks. Strategies for staying ahead include:
1. Threat Intelligence
Leveraging threat intelligence can help organizations stay informed about the latest vulnerabilities and attack vectors. By understanding emerging threats, businesses can take proactive measures to protect sensitive information.
2. Continuous Monitoring
Implementing continuous monitoring practices allows organizations to detect suspicious activities and potential breaches in real time. This proactive approach enables businesses to respond quickly and mitigate risks before they escalate.
Engaging with Third-Party Vendors
Many businesses rely on third-party vendors for various services, but this also introduces additional risks to data protection. Organizations should adopt the following strategies when engaging with third-party vendors:
1. Vendor Risk Assessment
Before partnering with a vendor, it is essential to conduct a thorough risk assessment to evaluate their data protection practices. This includes reviewing their security measures, compliance with regulations, and incident response capabilities.
2. Contractual Protections
Contracts with third-party vendors should include clauses that outline data protection responsibilities and breach notification procedures. These contractual protections help ensure that vendors take data security seriously.
Conclusion
As we navigate the complexities of data protection in 2025, businesses must adopt a proactive and comprehensive approach to safeguard sensitive information. By understanding regulatory frameworks, implementing robust security measures, and fostering a culture of data protection, organizations can effectively mitigate risks and build trust with their customers. In an era where data is a valuable asset, prioritizing data protection is not just a legal obligation but a fundamental business strategy for success.
Explore
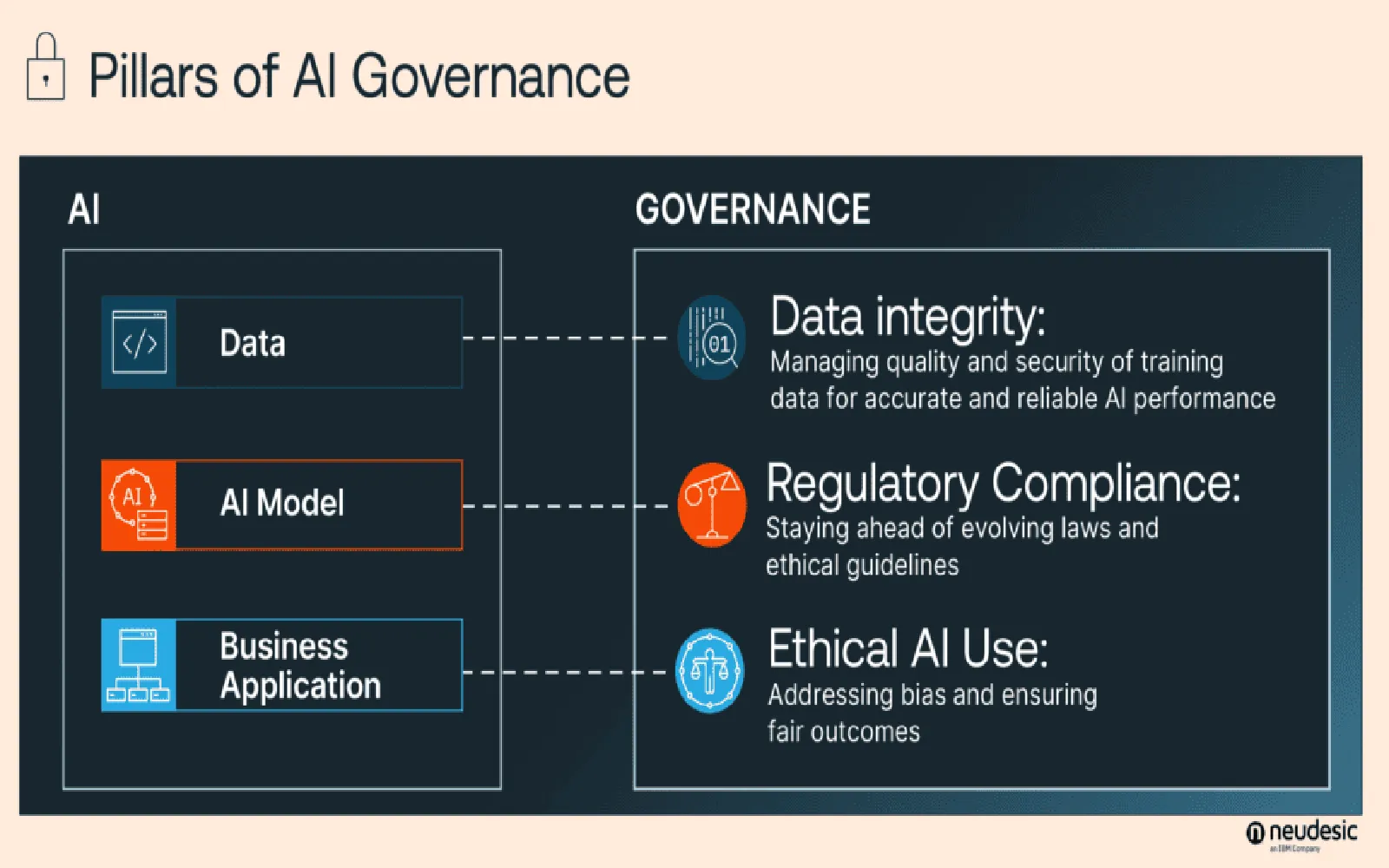
Navigating AI Governance in 2025: Strategies for Ethical and Responsible AI Development

Navigating Student Loans in 2025: Essential Tips for Future Borrowers
Top Data Management Software for Small Businesses in 2025: Boost Efficiency and Drive Growth

Sell Your House Fast in 2025: Proven Strategies to Get Top Dollar Quickly

Top Social Media Marketing Companies to Watch in 2025: Trends, Strategies, and Success Stories

2025 Advances in Psoriasis Treatment: Cutting-Edge Therapies and Effective Management Strategies

Top Trends for High Net Worth Financial Advisors in 2025: Strategies for Success

2025 Guide to Personal Loans for Debt Consolidation: Smart Strategies for Financial Freedom
